

CVE Analysis: Hacking a Crypto Network for Profit
By Zeyad Azima IntroductionWelcome, everyone. In this blog post, I will share the story of how, in June 2023, I successfully dumped the database of a crypto network, ultimately leading to the ability to achieve remote code execution. This was accomplished during my research and analysis of a CVE affecting one of Apache’s products. About the CVECVE-2022-227..
Read more

CVE-2023-26818 macOS TCC Bypass Exploit (Parts 1 & 2)
By Zeyad Azima OverviewThis combines both parts of the original write-up into a single post. Part 1 covers entitlement-targeted payloads (camera, microphone, Apple Events) for Telegram; Part 2 extends the tooling with data exfiltration and a console app for quicker dylib edits and compilation. Part 1 — Exploit Writing: CVE-2023-26818 macOS TCC Bypass w&#x..
Read more

CVE-2023-26818 macOS TCC Bypass Analysis (Parts 1 & 2)
By Zeyad Azima OverviewThis merges the two-part analysis of CVE-2023-26818 into a single post. Part 1 covers the root cause and DyLib injection path in Telegram. Part 2 dives into macOS sandboxing and how to bypass it to complete the exploit chain. Part 1 — CVE-2023-26818: macOS TCC Bypass w/ Telegram (Analysis)IntroductionA vulnerability Discovered ..
Read more

CVE-2021-38294: Apache Storm Nimbus Command Injection
By Zeyad Azima Introduction#CVE-2021-38294 is a Command Injection vulnerability that affects Nimbus server in apache storm in getTopologyHistory services, A successful crafted request to Nimbus server will result in exploitation for this vulnerability will lead to execute malicious command & takeover the server. The affected versions are 1.x prior to 1..
Read more

CVE-2021-44521: Apache Cassandra Remote Code Execution
By Zeyad Azima IntroductionCVE-2021-44521 is a vulnerability discovered in Apache Cassandra which allow an attacker to achieve remote command execution through UDFS & bypass the sandbox to execute the code on the server under specific configurations which let the attacker to takeover the server. CVSS:(Critical) https://nvd.nist.gov/vuln-metrics/cvss/v3..
Read more

CVE-2021-45232: Apache APISIX Dashboard Unauthorized Access & Unauth-RCE
By Zeyad Azima IntroductionApache APISIX Dashboard before 2.10.1 is vulnerable to Unauthorized Access Vulnerability known as CVE-2021-45232, The authentication middleware was developed based on the droplet framework. But, some APIs used the gin framework directly as a results it leads for a bypass in authentication & a successfully exploitation for thi..
Read more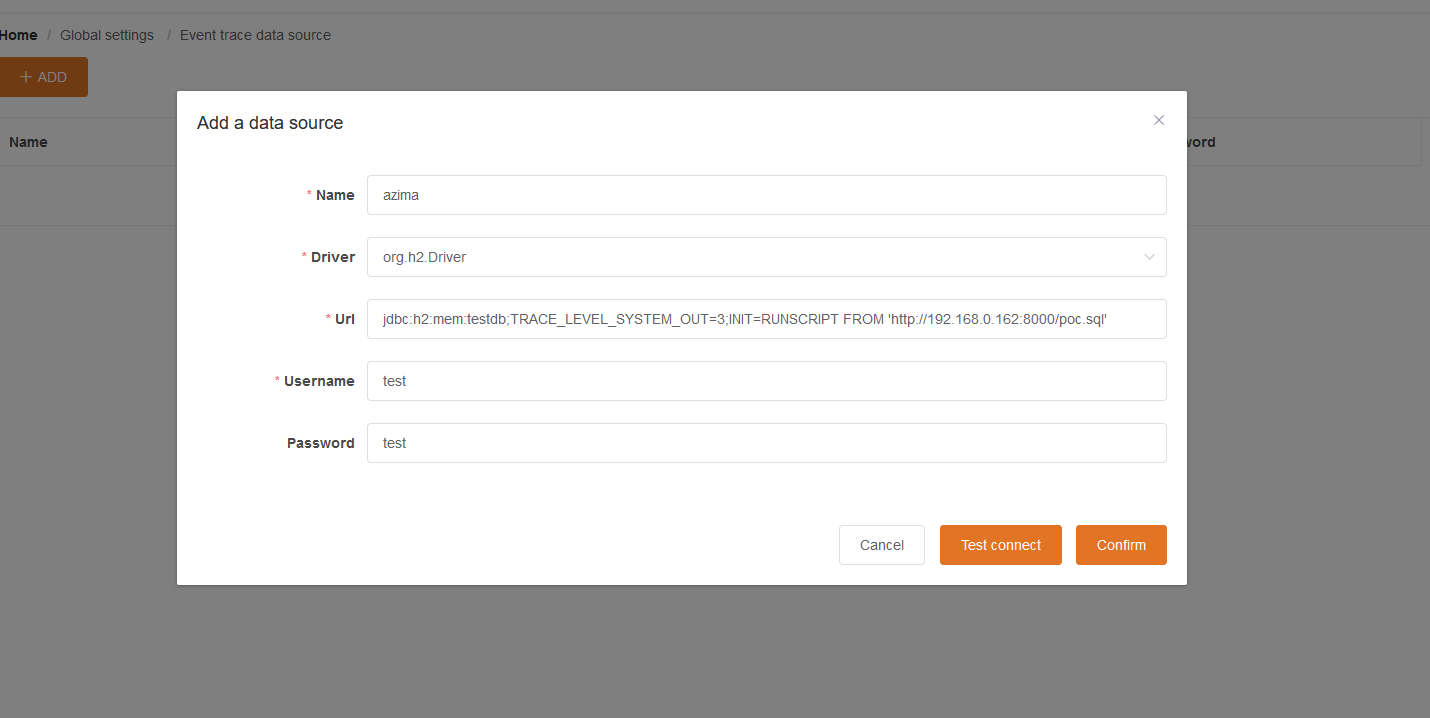

Exploit Writing: CVE-2022-22733 Privilege Escalation & RCE
By Zeyad Azima IntroductionIn the previous blog from here, We have done analysis for CVE-2022-22733 and understand the root cause of the vulnerability & the issue in details. Now, It’s the time to develop an exploit for this vulnerability and take it more further than just escalating our privileges. The ExploitAs we know from the analysis that to explo..
Read more

CVE-2022-22733: Apache ShardingSphere ElasticJob-UI privilege escalation
By Zeyad Azima IntroductionA vulnerability discovered in Apache ShardingSphere ElasticJob-UI known as CVE-2022-22733, The vulnerability lead to exposure of sensitive informatiopns and as a results it allows an attacker who has guest account to do privilege escalation. Testing LabFor the testing lab the vulnerability affecting version 3.0.0 and prior versio..
Read more

CVE-2023-24815: Vert.x-Web Path Traversal Escape
By Zeyad Azima IntroductionA vulnerability discovered in Vert.x-Web known as CVE-2023-24815, a threat actor can exploit this vulnerability to escape the path filter leading to exfiltrate any class path resource or Path Traversal, When tunning on windows. CVE Information CVE-ID: CVE-2023-24815 NVD Published Date: 02/09/2023 NVD Last Modified: 02..
Read more

CVE-2021-42885: deviceMac Remote Command Injection
By Zeyad Azima IntroductionA vulnerability discovered in TOTOLINK EX1200T model known as CVE-2021-42885 which is a remote command injection through the deviceMac parameter, As a results a malicious user can control the device and achieve remote command execution RCE. (Note:Everything you obtain here is for educational purposes, Don't use or abuse any b..
Read more